Hacking a website using Havij SQL injection:Full method for beginners
Now Lets start---->
Things you will need -->
1. Havij SQL injection Tool, download it from here cracked version
2. A sql vunerable site, I am taking this site
http://toyonorte.com.co/catalogo_nuevos_...e.php?id=2 as an example.
Checking for sql vulnerability --->
Here i am taking http://toyonorte.com.co/catalogo_nuevos_detalle.php?id=2 as an example.
Now to check is this site vulnerable to sql, I will simply add ' after the site url
like this http://toyonorte.com.co/catalogo_nuevos_detalle.php?id=2'
and i get this error on the site
You have an error in
your SQL syntax; check the manual that corresponds to your MySQL server
version for the right syntax to use near '\'' at line 1It means that site is vulnerable to sql injection.
Exploiting the vulnerable site --->
1. Open Havij and paste site url in target field and hit enter
2. Now wait for Havij to get all the databases of the website.
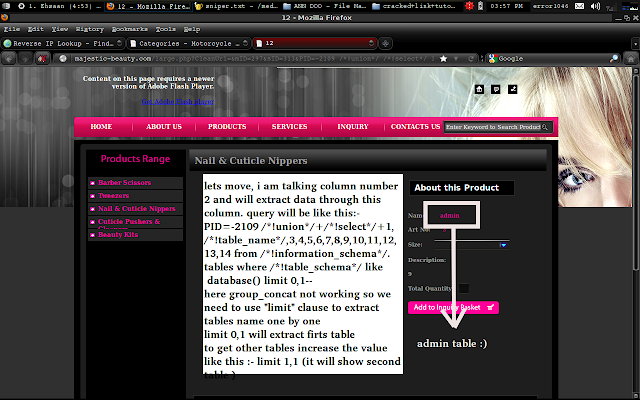
3. Now click on available databse of site and click on Get Tables like i am gonna
select535480_toyonorte of my site like in image.
![[Image: post.jpg]](http://s22.postimg.org/9b4os2lk1/post.jpg)
4. By clicking Get Tables Havij will look after the tables available in the database.
5. Now after the scanning Havij will get all tables, now the main work start , you have
to check it there table available named as admin, users and something
similar to these words like i get usuario in my website and select it and click on Get Columns. Like in pic given below.
![[Image: post2.jpg]](http://s8.postimg.org/uxfxz29np/post2.jpg)
6. Now after clicking Get Columns havij will get all the columns available in users table.
7. In my case i found diffrent columns like id, login, pass an many more.
8. Now select the columns and click on Get Data like in pic given below.
![[Image: post3.jpg]](http://s11.postimg.org/ofqf43643/post3.jpg)
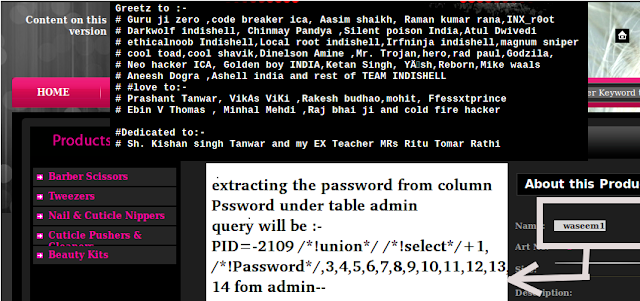
9. Now havij will look after the data available in columns login and password i.e admin username and passowrd like i get
username --> admin password--> 21232f297a57a5a743894a0e4a801fc3 (in encrypted form)
Like in image below
![[Image: post4.jpg]](http://s10.postimg.org/p0tspipbt/post4.jpg)
10. Now after i get
username and password there is a problem that passowrd i s encrypted in
mdm language , so we have to crack it .
11. To crack encrypted password just copy password click on MD5 tab in havij and paste the encrypted password in MD5 hash field and hit start.Now havij will try to crack the password. Like i cracked in image given below.![[Image: post5.jpg]](http://s23.postimg.org/oy61zobzf/post5.jpg)
12. Now i get Password cracked as admin.
13. Now we will check for admin panel where we gonna login with username and passoword.
In my case i found http://toyonorte.com.co/admin/ as admin panel, now open it in a web browser and login with username and password and now you are in admin panel.
Credits Zoombie hacker
Now Lets start---->
Things you will need -->
1. Havij SQL injection Tool, download it from here cracked version
2. A sql vunerable site, I am taking this site
http://toyonorte.com.co/catalogo_nuevos_...e.php?id=2 as an example.
Checking for sql vulnerability --->
Here i am taking http://toyonorte.com.co/catalogo_nuevos_detalle.php?id=2 as an example.
Now to check is this site vulnerable to sql, I will simply add ' after the site url
like this http://toyonorte.com.co/catalogo_nuevos_detalle.php?id=2'
and i get this error on the site
You have an error in
your SQL syntax; check the manual that corresponds to your MySQL server
version for the right syntax to use near '\'' at line 1It means that site is vulnerable to sql injection.
Exploiting the vulnerable site --->
1. Open Havij and paste site url in target field and hit enter
2. Now wait for Havij to get all the databases of the website.
3. Now click on available databse of site and click on Get Tables like i am gonna
select535480_toyonorte of my site like in image.
![[Image: post.jpg]](http://s22.postimg.org/9b4os2lk1/post.jpg)
4. By clicking Get Tables Havij will look after the tables available in the database.
5. Now after the scanning Havij will get all tables, now the main work start , you have
to check it there table available named as admin, users and something
similar to these words like i get usuario in my website and select it and click on Get Columns. Like in pic given below.
![[Image: post2.jpg]](http://s8.postimg.org/uxfxz29np/post2.jpg)
6. Now after clicking Get Columns havij will get all the columns available in users table.
7. In my case i found diffrent columns like id, login, pass an many more.
8. Now select the columns and click on Get Data like in pic given below.
![[Image: post3.jpg]](http://s11.postimg.org/ofqf43643/post3.jpg)
9. Now havij will look after the data available in columns login and password i.e admin username and passowrd like i get
username --> admin password--> 21232f297a57a5a743894a0e4a801fc3 (in encrypted form)
Like in image below
![[Image: post4.jpg]](http://s10.postimg.org/p0tspipbt/post4.jpg)
10. Now after i get
username and password there is a problem that passowrd i s encrypted in
mdm language , so we have to crack it .
11. To crack encrypted password just copy password click on MD5 tab in havij and paste the encrypted password in MD5 hash field and hit start.Now havij will try to crack the password. Like i cracked in image given below.
![[Image: post5.jpg]](http://s23.postimg.org/oy61zobzf/post5.jpg)
12. Now i get Password cracked as admin.
13. Now we will check for admin panel where we gonna login with username and passoword.
In my case i found http://toyonorte.com.co/admin/ as admin panel, now open it in a web browser and login with username and password and now you are in admin panel.
Credits Zoombie hacker